The viral loop protocol: Engineering organic magnetism

The Viral Loop Protocol is the systematic engineering of product mechanics where a user’s natural usage creates an External Trigger for a new user.
What I am defining here is not a marketing trick, even if its sounds like one; it represents the Physics of Attraction embedded into the code.
Newcomers called it “going viral.” For strategic leaders, it involves designing a Self-Perpetuating Cycle in which growth depends on utility rather than force.
The contextual decay: Why forced distribution has failed
Forced distribution has failed because it ignores the fundamental rule of Social Capital: High-value users do not share content to help you; they share to signal their own identity.
The “Share” button is an artifact of desperation. When you rely on Forced Distribution (e.g., “Invite 5 friends to unlock”), you lower the status of the product. You must replace the “Ask” with the “Asset.”
You must orchestrate a scenario where not sharing the product feels like a loss of value for the user.
But how do you architect this magnetic cycle? The answer lies in a precise sequence.
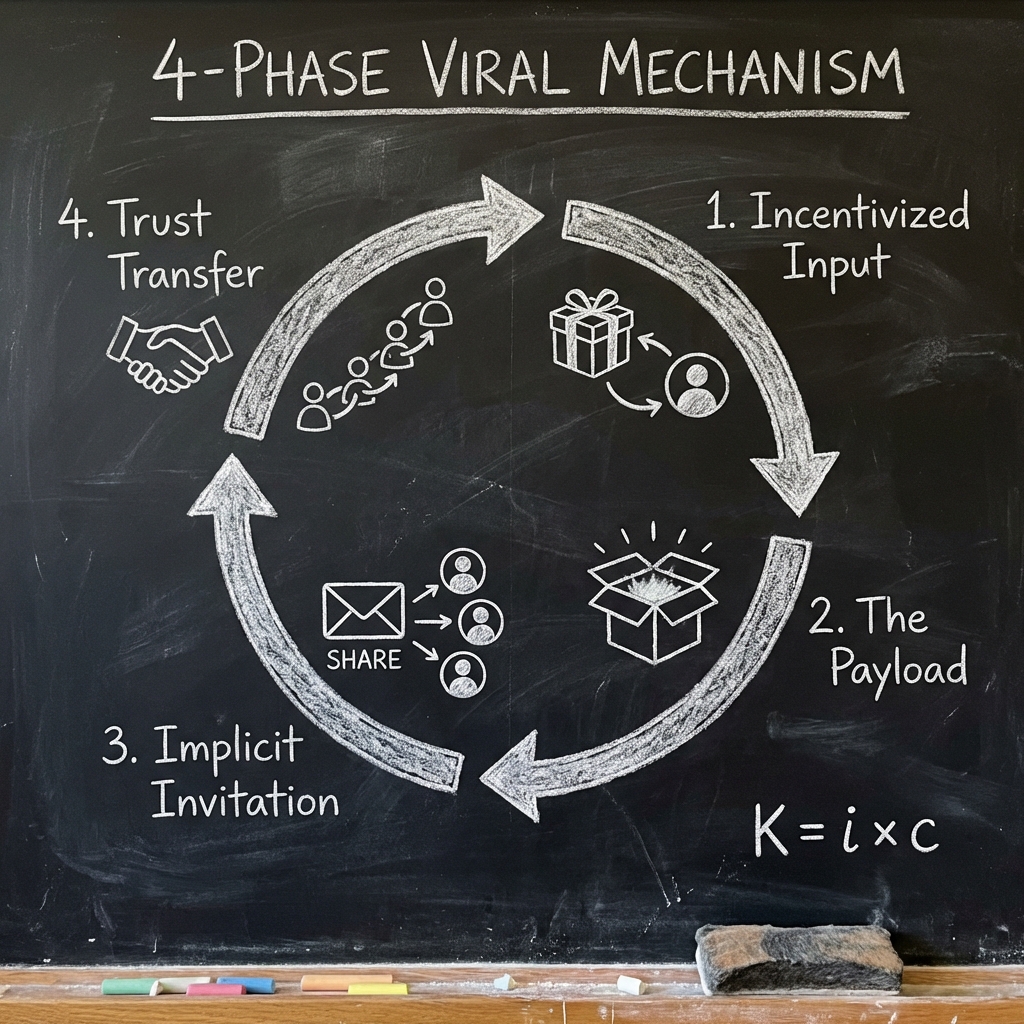
The four phases of algorithmic seduction
To orchestrate a true Viral Loop, you must adhere to a strict sequence of seduction; a Biological Function embedded into the product architecture:
- Incentivized Input: The user takes a selfish action to solve a personal problem (e.g., Uploading a file to Dropbox).
- The Value Payload: The system processes the input and creates a unique asset (e.g., A shareable link or a visualized data chart).
- The Implicit Invitation: To realize the full value of the Payload, the user must invite another. The invitation is not a request; it is a necessity of the workflow.
- The Trust Transfer: The recipient receives the Payload from a trusted peer, not a brand advertisement. This bypasses skepticism and converts the External Trigger into a new Incentivized Input.
But understanding the loop is not enough. You must quantify its magnetism.
The viral coefficient: Measuring magnetism
The Viral Coefficient (K-Factor) is the mathematical signature of your loop’s power. It measures how many new users each existing user generates through the protocol.
The Formula: K = i × c
Where i is the number of invitations sent per user, and c is the conversion rate of those invitations.
- K > 1: Exponential growth. The loop is self-perpetuating.
- K = 1: Stasis. You are replacing churn, not growing.
- K < 1: Decay. Your loop is leaking energy.
To the uninitiated, “going viral” is a stroke of luck. To the strategic leader, it is the disciplined pursuit of K > 1.
The second variable is Cycle Time, how long it takes for one loop to complete. A K of 1.2 with a 3-day cycle will outpace a K of 1.5 with a 30-day cycle. Speed compounds.
Yet even a high K-Factor can be confused with a different phenomenon entirely.
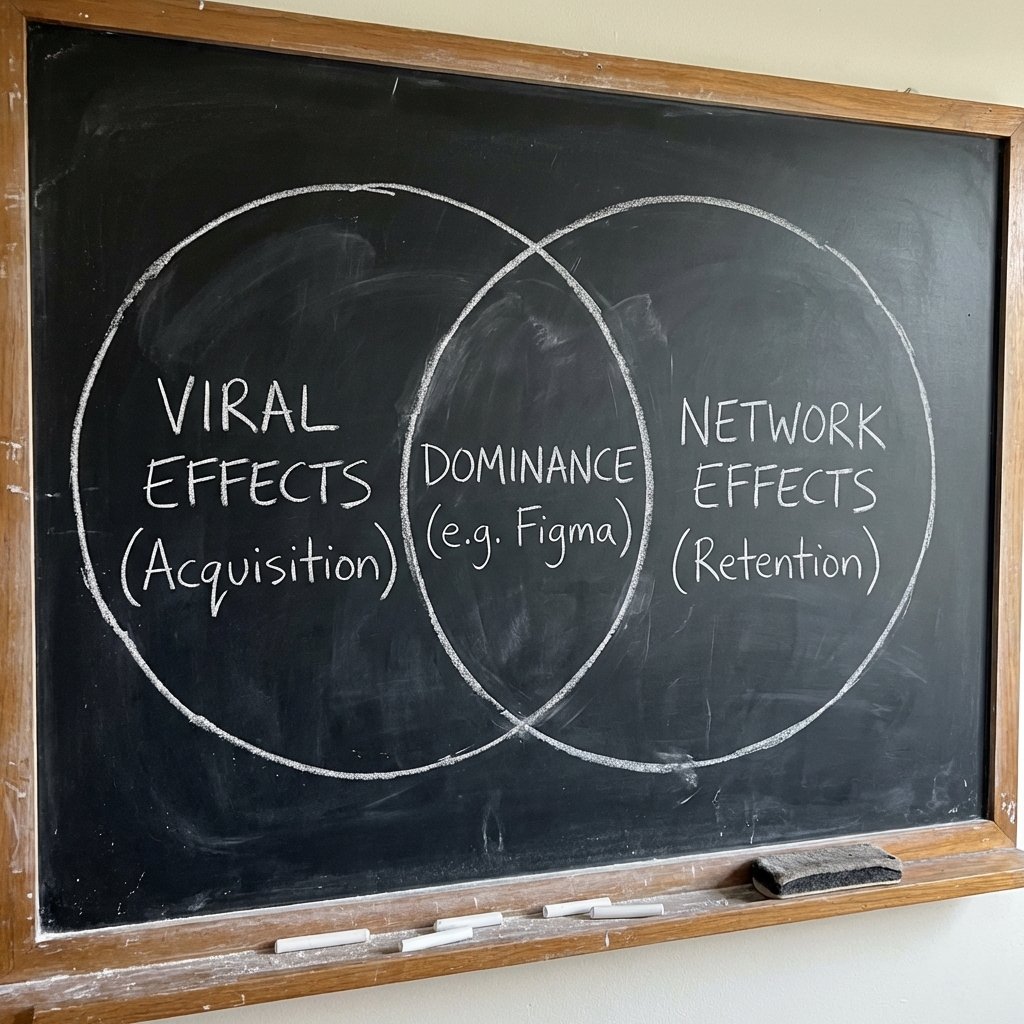
Network effects vs viral effects: The critical distinction
Viral Effects and Network Effects are not synonyms. Conflating them is a strategic error.
- Viral Effects: mean you acquire users for free. The product spreads. (e.g., A watermark on a generated image.)
- Network Effects: mean the product becomes more valuable as more people use it. (e.g., Slack is useless alone; it becomes indispensable when your team is on it.)
The highest-leverage products combine both: Figma spreads virally through shared design links (Viral), and becomes locked-in because design systems require collaboration (Network).
If you have only Viral, you get a spike and a fade. If you have only Network, you grow slowly but retain deeply. If you have both, you have architected dominance.
Even with both forces aligned, loops are fragile. They can collapse.
The failure modes: Why loops collapse
A Viral Loop collapses when friction exceeds the perceived value of the Payload.
The three common failure modes:
- Friction in the Invitation: If sharing requires more than two clicks, the loop dies. Every form field is a leak.
- Low Payload Value: If the recipient sees the shared asset and thinks “So what?”, the Trust Transfer fails. The asset must be immediately valuable to the recipient, not just the sender.
- Trust Decay: If the sender feels embarrassed or “spammy” for sharing, they will not share again. You must ensure the act of sharing raises the sender’s status, not lowers it. This requires reducing the cognitive friction of the interface.
Audit your loop. Identify where energy is bleeding out.
The Viral Loop creates more than just users. It creates a semantic footprint in the Knowledge Graph.
Far from being mere theory, this viral loop is a well-documented rhythm of human behavior—amplified by the invisible hand of algorithms.
The scientific validation: Why the physics hold true
The seminal research of Leskovec, Adamic, and Huberman (2005), validated the Viral Loop mechinics. They analyzed 16 million recommendations to map the dynamics of information diffusion.
Their findings confirm that virality is not a random occurrence but a function of three specific scientific levers:
- Signaling Theory: Consumption choices are used to communicate unobservable qualities (status, values, competence). Products that go viral do so because they act as a high-fidelity Identity Signal (Berger, 2013).
- Social Capital Mobilization: Sharing behavior is driven by the desire to mobilize Structural and Relational Capital. If the sharing act increases the user’s perceived authority within their network, the K-Factor accelerates.
- The Contextual Edge: Research shows that recommendations for “High-Context” or “Technical” products in small, dense communities are significantly more effective than mass-market broadcast. This validates the focus on Topical Authority rather than broad reach.
These are the Sociological Mandates that determine product survival in a post-AI search landscape.
Beyond social growth, these validated loops generate the ultimate data signal for machine intelligence: a semantic footprint in the Knowledge Graph.
The semantic imprint: User entities as signal
Your users are quietly building your authority: every time they connect with your content, they’re reinforcing a semantic bridge between your brand and key topics in the Knowledge Graph.
In the old world, you begged websites for backlinks. In the Semantic Web, you map User Entities to your Brand Entity. This is the shift towards entity-based authority.
- Subject:
[User Name] - Predicate:
is_user_of - Object:
[Your Brand]
When a user shares a generated report publicly, they are validating your entity. To the Knowledge Graph, a brand cited by thousands of real, verifiable human nodes is not just a website; it is an Authority.
To activate this at scale, you must create the mechanism that transforms user behavior into shareable status.
Orchestrating the identity mirror
The most powerful application of this protocol is the Identity Mirror, a mechanism where the product analyzes user data to generate a reflection that makes the user look exceptional.
The “Stat Sheet” Strategy:
You must create a “Report Card” that transforms user behavior into a Competence Signal (e.g., Spotify Wrapped, GitHub Contributions).
When a user shares this mirror, they are not advertising your product; they are broadcasting their own status. Your brand logo is simply the watermark on their success.
This is the ultimate form of The Zero-Click Protocol, content that lives on social feeds, creating desire without requiring a click.
With the mechanics understood, the final question is one of organizational will.
The strategic mandate: Build, don’t beg
True growth begins when you stop chasing clicks and start asking your team this:
“Does using our product spark that ‘I have to share this!’ feeling?”
If not, then, you don’t have a marketing problem, you have a Utility Deficit.
Heal the heart of your product, and the word-of-mouth will flow on its own.
Share Article
If this article helped you, please share it with others!
Some content may be outdated
